[ad_1]
xssfox
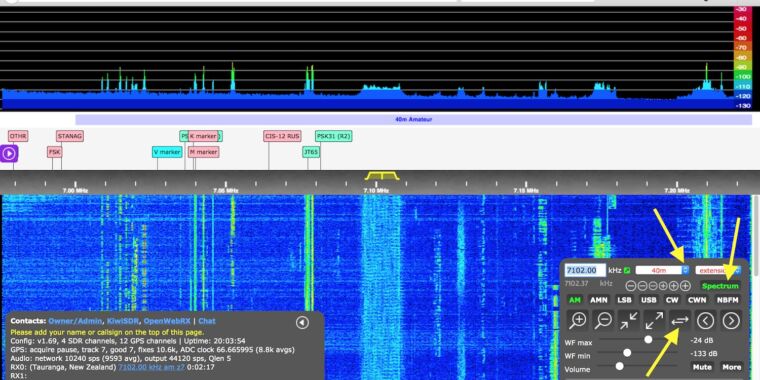
KiwiSDR is {hardware} that makes use of a software-defined radio to watch transmissions in a neighborhood space and stream them over the Web. A largely hobbyist base of customers does every kind of cool issues with the playing-card-sized units. As an example, a consumer in Manhattan might join one to the Web so that individuals in Madrid, Spain, or Sydney, Australia, might take heed to AM radio broadcasts, CB radio conversations, and even watch lightning storms in Manhattan.
On Wednesday, customers realized that for years, their units had been geared up with a backdoor that allowed the KiwiSDR creator—and probably others—to log in to the units with administrative system rights. The distant admin might then make configuration adjustments and entry knowledge not only for the KiwiSDR however in lots of instances to the Raspberry Pi, BeagleBone Black, or different computing units the SDR {hardware} is related to.
A giant belief drawback
Indicators of the backdoor within the KiwiSDR date again to at the least 2017. The backdoor was not too long ago eliminated with no point out of the elimination underneath unclear circumstances. However regardless of the elimination, customers stay rattled for the reason that units run as root on no matter computing system they’re related to and might typically entry different units on the identical community.
“It’s a giant belief drawback,” a consumer with the deal with xssfox instructed me. “I used to be utterly unaware that there was a backdoor, and it’s massively disappointing to see the developer including backdoors in and actively utilizing them with out consent.”
Xssfox stated she runs two KiwiSDR units, one on a BeagleBone Black that makes use of a customized FPGA to run the Satisfaction Radio Group, which lets folks take heed to radio transmissions in and round Gladstone, Australia. A web page of public broadcasts exhibits that roughly 600 different units are additionally related to the Web.
Xssfox added:
In my case, the KiwiSDRs are hosted on a distant website that has different radio experiments working. They might have gained entry to these. Different KiwiSDR customers generally have them arrange in distant places utilizing different folks’s/firms’ networks, or on their residence community. It’s kind of just like the safety digicam backdoors/exploits, however smaller-scale [and] simply beginner radio folks.
Software program-defined radios use software program—quite than the usual {hardware} present in conventional radio tools—to course of radio alerts. The KiwiSDR attaches to an embedded laptop, which in flip shares native alerts with a a lot wider base of individuals.
The backdoor is straightforward sufficient. A number of strains of code permit the developer to remotely entry any system by coming into its URL in a browser and appending a password to the top of the tackle. From there, the particular person utilizing the backdoor could make configuration adjustments not solely to the radio system however, by default, additionally to the underlying computing system it runs on. Right here’s a video of xssfox utilizing the backdoor on her system and getting root entry to her BeagleBone.
Fast video displaying how the backdoor on the kiwisdr works.
I’ve additionally examined that contact /root/kiwi.config/decide.no_console mitigates the problem
Thanks @the6p4c for serving to me check 🙂 pic.twitter.com/0xKD1NfvwL
— xssfox (@xssfox) July 15, 2021
Right here’s a picture in larger decision:
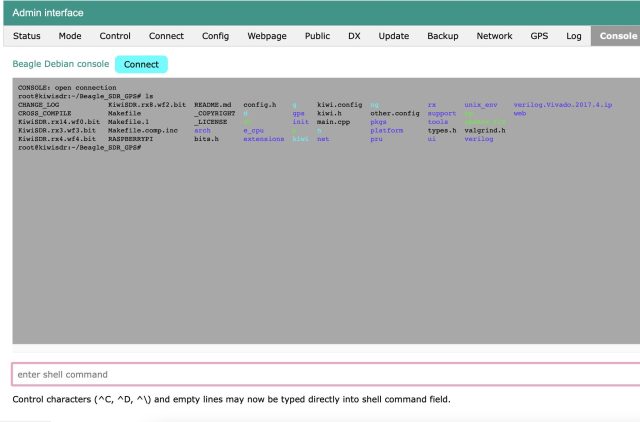
“It appears just like the SDR… plugs right into a BeagleBone Arm Linux board,” HD Moore, a safety knowledgeable and CEO of community discovery platform Rumble, instructed me. “This shell is on that Linux board. Compromising it could get you into the consumer’s community.”
The backdoor lives on
Xssfox stated that entry to the underlying computing system—and probably different units on the identical community—occurs so long as a setting referred to as “console entry” is turned on, as it’s by default. Turning the entry off requires a change to both the admin interface or a configuration file, which many customers are unlikely to have made. Moreover, many units are up to date hardly ever, if ever. So regardless that the KiwiSDR developer has eliminated the offending code, the backdoor will stay on in units, making them susceptible to takeover.
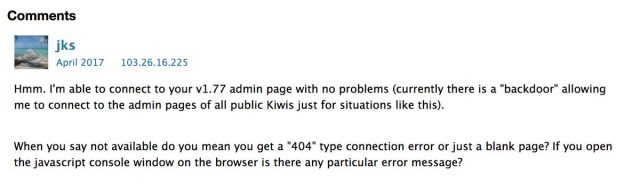
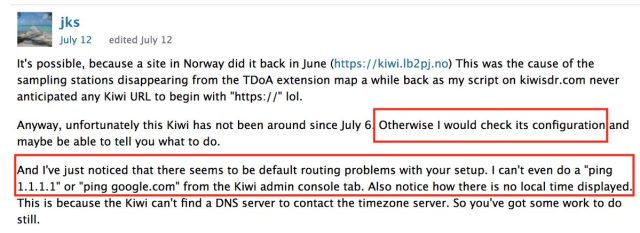
Software program submissions and technical paperwork like this one title the developer of KiwiSDR as John Seamons. Seamons didn’t reply to an e-mail searching for remark for this put up.
The consumer boards have been unavailable on the time of publication. Screenshots here and here, nevertheless, seem to point out Seamons admitting to the backdoor as way back as 2017.
One other troubling side to the backdoor is that, as noted by engineer consumer Mark Jessop, it communicated over an HTTP connection, exposing the plaintext password and knowledge over the backdoored community to anybody who might monitor the visitors coming into or out of the system.
Nevertheless, given the KiwiSDR is HTTP solely, sending what is basically a ‘grasp’ password within the clear is a little bit worrying. KiwiSDR doesn’t help HTTPS, and it has been acknowledged that it’ll by no means help it. (Coping with certs on it might be a PITA too)
— Mark Jessop (@vk5qi) July 14, 2021
KiwiSDR customers who wish to verify if their units have been remotely accessed can achieve this by working the command
zgrep -- "PWD admin" /var/log/messages*
There’s no indication that anybody has used the backdoor to do malicious issues, however the very existence of this code and its obvious use through the years to entry consumer units with out permission is itself a safety breach—and a disturbing one at that. At a minimal, customers ought to examine their units and networks for indicators of compromise and improve to v1.461. The really paranoid ought to think about unplugging their units till extra particulars change into obtainable.
Itemizing picture by KiwiSDR
[ad_2]
Source link